I was thinking to write about the 4-way handshake and started to think that from where I should start writing. Shall I just describe 4-way handshake which can be found everywhere on the web or shall I do a deep dive? Reason for me to write is to make it easier to understand for non WiFi people who can just read and understand because sometimes different terminologies used in this process can be confusing. So, let’s start with…
What is 4-way Handshake:
The 4-way handshake is the process of exchanging 4 messages between an access point (authenticator) and the client device (supplicant) to generate some encryption keys which can be used to encrypt actual data sent over Wireless medium. These keys which are generated through 4-way handshake are generated by some source key material which will be discussed later.
If you do not want to get confused about the terminologies used in 4-way handshake then let’s have a quick look. Let’s see what terminologies we might come across to understand 4-way handshake. I would say don’t be scared of these terminologies. It’s like much ado about nothing.

These are the few keys we will be discussing…
- MSK (Master Session Key)
- PMK (Pairwise Master Key)
- GMK (Group Master Key)
- PTK (Pairwise Transient Key)
- GTK (Group Temporal Key)
- ANonce
- SNonce
- MIC
I will start by talking about the keys which are generated during the 4-way handshake and towards the keys and other variables needed in order to generate these keys.
PTK (Pairwise Transient Key):
Pairwise Transient key is used to encrypt all unicast traffic between a client station and the access point. PTK is unique between a client station and access point. To generate PTK, client device and access point need the following information.
PTK = PRF (PMK + Anonce + SNonce + Mac (AA)+ Mac (SA))
Anonce is a random number generated by an access point (authenticator), Snonce a random number generated by the client device (supplicant). MAC addresses of supplicant (client device) and MAC address of authenticator (access point). PRF is a pseudo-random function which is applied to all the input.
PTK is dependent on another high-level key PMK (pairwise master key) which is discussed below.
GTK (Group Temporal Key):
Group temporal key is used to encrypt all broadcast and multicast traffic between an access point and multiple client devices. GTK is the key which is shared between all client devices associated with 1 access point. For every access point, there will be a different GTK which will be shared between its associated devices.
GTK is dependent on another high-level key GMK (group master key) discussed below.
PMK (Pairwise Master Key):
What is PMK and why we need it? Now we know what is PTK and GTK. PTK is generated with the help of PMK. As we discused above in order to generate PTK, we need the following input.
PTK = PRF (PMK + Anonce + SNonce + Mac (AA)+ Mac (SA))
Pairwise master is key generated from master session key (MSK). In case of WPA2/PSK when device authenticates with access point the PSK becomes PMK.
Point to Remember: PMK resides on all stations as in AP and client devices, so we do not need to share this information. We use this information to create PTK which are used for unicast data encryption.
GMK (Group Master Key):
Group master key is used in a 4-way handshake to create GTK discussed above. GTK is generated on every access point and shared with the devices connected to this AP.
MSK (Master Session Key):
The master session is the first key which is generated either from 802.1X/EAP or derived from PSK authentication.
We discussed above keys from bottom to top and how keys are dependent on other keys. This is the view from top to bottom.
- The first level key is generated is MSK during the process of 802.1X/EAP or PSK authentication.
- The second level key is generated from MSK is PMK and GMK. PMK is used to generate PTK and GMK is used to create GTK.
- Third level keys are the actual keys used for data encryption.

(Keys Hierarchy)
4-Way Handshake in Action:
Once we understand important keys and how they are generated now let’s have a look on an actual 4-way handshake. Imagine an access point is configured with WPA2/PSK and device is trying to connect to it. In our example its SSID PRINTERS with password printer123.


Sooner user click on printers SSID it goes through the states which I have discussed in another post. From authentication to the association to security validation. This is where 4-way handshake happens, instead of sending the password to the access points there are EAPOL (Extensible authentication protocol over LAN) messages exchange happens.

(4-way handshake)
Device States:
A device going through states from authentication to association. Once the device is authenticated and associated and now security will be checked, and 4-way handshake will start.

4-way handshake Wireshark view:

Message1: access point sends EAPOL message with Anonce (random number) to the device to generate PTK. Don’t forget client device knows Ap’s MAC because its connected to it. It has PMK, Snonce and its own MAC address. Once it receives Anonce from access point it has all the inputs to create the PTK.
PTK = PRF (PMK + Anonce + SNonce + Mac (AA)+ Mac (SA))
Mac address 9c:5d:12:5e:6c:66 is source address or mac address of the access point who is sending first EAPOL message to the device and d0:c5:f3:a9;16:c5 is Mac device. In this message access point sending ANonce to the client device.
![]()
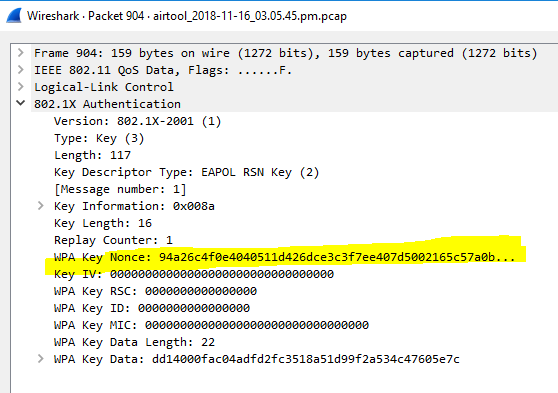
(Anonce from AP to the device)
Message2: Once the device has created its PTK it sends out SNonce which is needed by the access point to generate PTK as well. The device sends EAPOL to AP message2 with MIC (message integrity check) to make sure when the access point can verify whether this message corrupted or modified. Once SNonce received by the AP it can generate PTK as well for unicast traffic encryption.
This is the second message going from the client device to AP with Snonce and MIC field set to 1.
![]()
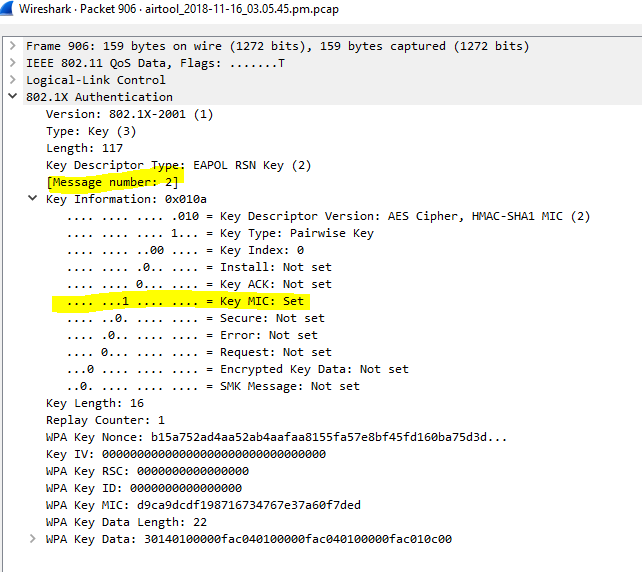
(Message 2)
Message3: EAPOL message3 is sent from AP to client device containing GTK. AP creates GTK without the involvement of the client from GMK.
![]()

(Message 3)
Message4: Fourth and last EPOL message will be sent from the client to AP just to confirm that Keys have been installed. ![]()
4-way handshake Result:
Control port unlocked: Once the 4-way handshake is completed successfully virtual control port which blocks all the traffic will be open and now encrypted traffic can flow. Now all unicast traffic will be encrypted with PTK and all multicast traffic will be encrypted via GTK which created in the 4-way handshake process.
Summary:
Lets summaries all this what we have discussed above. I have broadcasted PRINTERS SSID and tried to connect to it. AP is beaconing SSIDs and when I clicked PRINTERS SSID to connect we can see full conversation with acknowledgment frame.
The device is requesting to connect to PRINTERS and the access point is responding with a probe response. Now device goes through the states from unauthenticated and un-associated to authenticated and associated.
Once authenticated and associated now it goes through security check and 4-way handshake happens and after successful 4-way handshake now the control port will be open for communication.

(Full conversation from association to complete 4-way handshake)
That was the best explanation i found online , thanks
Thank you so much for your interpretation.
Excellent. your explanation is crystal clear.
Thank you
Thanks!
Pingback:Kali Linux on RasperryPi – Understand 802.11 – CUNG HOC ESP32
The best explanation. I understood and on the way to pass the exams
Came here looking for the meaning of Anounce and Snounce and just got lost in the superb explanation until now, its when I remembered what I was looking for.
Nice one, Thank you.
super explanation, that to also, i never seen before in my life.
It’s good
You should explain in more detail how MSK, PMK and GMK are created.
Thanks for the great article. However, it is still unclear how (or at what step) the password “printer123” is used. Can you explain?
Amazing explanation this is what I was searching for.
But could you explain where the password “printer123” Is used in 4-way handshake or is it after that?
@jahanzab I got the answer for our question. It is available in quora.
MIC and KCK is the answer.
AP knows the password because we stored the password (your wifi password) in AP configuration page.
PMK is generated by encrypting the password and then send over by PTK. Here MIC needs to validate the code at Access Point and at Client. That means MIC carries the encrypted password which was created by KCK (key confirmation key).
Now let’s say using aireplay we capture the handshake and CAP file is stored offline.
Aircrack brute force will create a virtual AP and Client in our PC and they will do the 4 way handshake but here each time a new MIC (password from brute force file) will be used to compare with actual MIC in CAP file. Once the password matches bruteforce will show the password.
Quora guy explained even in more detail. Check out his answer
@gameon, I also have the same question, can you link to the Quora answer?
Also, I understand all 4 messages but I don’t see how both ends apply the “PRF”. The post says “PRF is a pseudo-random function which is applied to all the input.”, but they are lot’s of them, how do they know what pseudo-random function to use for the given inputs.
Great article, thanks and keep it up!
very good one. Thanks
hey can anybody help me out , i want to know that do wep also used 4 way handshake. I know that wpa/wpa2 uses it but what about “wep”.
When do the EAPOL_START message is send from supplicant to AP? Is it immediately after the the authorization and association? Does all devices send EAPOL_START?
Where does PBKDF2 come in to this?
My Question is , how MIC value is calculated in 3 Msgs (Msg2-4) and validated at opposite ends ? If any new client joins the BSS , Will AP generate new GTK and shared with all clients or already cretaed GTK shared to the new client ?
hi, so where is AES used in the 4 way handshake?
i though PTK is xor stream cipher, isn’t it?
perfect! thank you
@Sandy
The authenticator sends an EAPOL – Key frame to the supplicant containing the ANonce, the authenticator ’ s RSN information element capabilities, and a MIC. This would be last verification before the key installed by the station.
Regarding GTK:
The authenticator can update the GTK for a number of reasons. For example, the authenticator may change the GTK on disassociation or deauthentication of a client station. WLAN vendors may also offer a configuration setting to trigger the creation of a new GTK based on a timed interval.
I don’t believe GTK will be changed if a new client is joining the BSS but certainly can be tested to verify that.
@Julio
This article might help understand how PRF function will be used…
http://etutorials.org/Networking/802.11+security.+wi-fi+protected+access+and+802.11i/Part+II+The+Design+of+Wi-Fi+Security/Chapter+10.+WPA+and+RSN+Key+Hierarchy/Computing+the+Temporal+Keys/
Hi @Alex Tse,
AES is not involved in the process of a 4-way handshake but being used for data encryption.
AES (Advanced Encryption Standard) is just the encryption method used in this security method.
So if I summarize:
IEEE 802.11 security has:
.Robust security network and Robust security network has:
.IEEE 802.1X (authentication with AD or server etc), TKIP and WPA2 etc.
.WPA2 mandates the use of a new protocol, counter mode with cipher-block chaining message authentication protocol (CCMP)and CCMP uses the AES block cipher.
It should be understood that AES is a standard and not a protocol. A protocol is a series of steps designed to achieve a specific end, while a standard is a set of rules and guidelines that define an overall design structure. The AES standard specifies the use of the Rijandel symmetric block cipher that can process data blocks of 128 bits, using cipher keys of 128, 192, and 256 bits.
It means it takes a text of 128bits and then use cipher keys of 128, 192, and 256 bits to change that text into cipher text so it can not be read by the intruders.
hope this helps.
Regards.
.
thanks
Thank you for this enriched post. I have a little question about the three keys that will eventually be derived from the PTK. One of them is called the EAPOL KEK, which is used for encrypting keys. My question is, when will KEK be used? and for what keys will it be protecting?
Thank you for spreading your knowledge,
HI,
I hope you are well.
Thanks for your question.
I think it’s good to discuss these topics openly like this so people can benefit from this.
as you know PTK is consists of 3 sections or Keys.
1- KCK (Key confirmation key): From the name confirmation you can guess that it is used to confirm something. so this is the key used during a 4-way handshake and group key handshake for data integrity.
2- KEK (Key encryption key): This key also used during a 4-way handshake and group key handshake for data privacy.
3- TK (Temporal Key): This key is used to encrypt and decrypts the actual payload between the station and the access point (supplicant).
you should be able to find this information in CWNP security book (CWSP).
Thank you for your reply. Regarding using those keys in the 4-way handshake, is it the same handshake explained in this site and the book as well? If so, I am confused about how we initially use those keys during the handshake while this handshake is supposed to generate them at the end.
Thank you again,
Hi,
I believe you are right to be confused once you start looking into the keys and the names. Different names confuse me all the time. I wish they can use easy (IN ENGLISH) terminologies.
PTK is not generated at the end of 4-way handshake but it will be created after message 1 and 2.
1- After message 1 Station has the required information to generate PTK so it can derive all other keys after message 1 of 4way handshake.
2- After message 2 of 4-way handshake now access point also has required information to generate PTK and then from PTK it can generate all other keys.
3- Message 3 is where GTK will be sent to the station and that’s where KEK will be used to encrypt GTK.
There is another blog which has written about further key generations. I believe It will answer your questions.
https://praneethwifi.in/2019/11/08/4-way-hand-shake-keys-generation-and-mic-verification/
Hi…
Great article…
I have doubts when we say the PTK or GTK will be, ” installed”. Consider if I am using a linux based system with a specific vendor chip.. Where exactly the interim or final keys are stored and how?
Hi Anjali,
As you know PTK and GTK are not permanent keys and will be changed depending on the situation.
If the device roams or disconnects then new keys will be generated. Keys are normally stored in the cache and will be dropped when there is a need for generating a new key.
Pingback:What Is WPA2 & How Do I Improve WPA2 Security? | InfoSec Insights
This is a fantastic article! You helped me narrow down the area for a problem I have had with my wifi connections!
Such a crisp, short and to the point explanation. One of the best articles out there on the 4 way handshake.
Hi All ,
I have one question , How PMK is different in WPA2-PSK from 802.1X Authentication ?
In personal mode , We simply give Passphrase/Password(PSK) to connect to AP . But how PMK derives from PSK. Can anyone explain ?
Thanks,
Sandy
Pingback:authentication - Why does message 1 of the WPA2 4 way handshake begin with the access point sending a random number? - New and Fresh Private + Public Proxies Lists Everyday!
I wonder what is MSK and how it affects the handshake, seems like there aren’t much info about it.
thank you
Hi. Thanks for the great article. I have one question:
What is “unicast”? (in the figure : 4 way handshake ) in some other places I have seen it as “counter” in the first 2 messages and then “counter+1” in the third.
Thanks.
Hi Bojan,
Unicast meaning in 1 particular direction.
in this case from station to AP or AP to station. so the destination is specified in unicast traffic.
so if someone writes as counter and counter+1 that is just a way of describing.
It’s because we have 4 key messages.
1- From AP to station
2- Station to AP
3- AP to station
4- station to AP (last message)
so you have 1 message counter and a reply to that message would be counter+1.
Where really authentication is done (type of message 1,2,3, or 4)?
Good article
This a real nice explanation. Thank you very much.
Great stuff……
These detailed explanations are freaking awesome – thanks for taking the time to publish them.
One note, and this is minor…I think the T in PTK stands for Transient instead of Transit.
thanks
Hi ,
I have one more question , Here in this process of 4-way handshake , Finally two temporal keys are generated along with KCK , KEK , KTK .
How these two temporal keys are used .
I expect One key is used for encrypt or decrypt the data . why other key again .
Is that one key for encrypt and other key for decrypt like this ?
Help on this .
Thanks in Advance
YOU NEED REAL VISITORS FOR: wifi-professionals.com ?
We Provide 100% Real Visitors To Your Website.
With this traffic, you can boost ranking in SERP, SEO, profit from CPM…
CLAIM YOUR 24 HOURS FREE TEST HERE=> https://zeep.ly/ka3Ur?32089
Pingback:Terzo incontro tecnici WLAN – WLAN Italia
I am lost trying to find how to reconfigure the pairwise cipher keys…help???
Pingback:Hacking WIFI: Cracking de WPA2 desde Python – MIC Cracking – La Cripta del Hacker
Pingback:Comparing the time to crack WPA2 password using different types of GPUs using hashcat – Futue Technology with KM
Pingback:CS 161 Notes: Lec 17-18 – silkrow's tech blog
Exellent, thank you very much for sharing!
Pingback:[Wi-Fi] 4-way handshake 802.11i Security | 選擇實驗室
Such a nice content.
This article is really well done, Wifi nerds salute you!
Pingback:Penetrating Networks by Cracking WPA2 – Blog | DigForCE Lab
Thank you so much for your interpretation.
Thank so much for the detailed explanation.
Thanks for taking the time to make this. Very useful and I feel I now have a better understanding of the keys and process.
966550073112
Thanks alot. Very good explanation.
steroid satın al ve anabolik steroid sipariş fiyatları
As a website owner you want to make money. Try our ads network program for Publishers and Advertisers. You receive 2 account in one, a Publisher account and Advertiser account coming with $5.00 as a bonus to promote your website in our network. Take a look.
let say we creat wireless access point and try to log clients they try to connect to it ,
how we able to log success/failed access ? ,and can we see the password sended to authenticate ?
if we can please i need a hint or guide ,or any source code related to this
Pingback:Basic WiFi cracking – ducanhthehacker
Great explanation
You’ve done an impressive work on your website in covering the topic. I am working on content about SEO and thought you might like to check out Webemail24 and let me what you think.
Thank you for sharing this information! If you need some details about Data Mining than have a look here Articleworld
Hi Jahanzeb,
Good question.
whole point of this process is to never share the password so password is never shared.
Access point knows the password. Device knows the password when we enter the password.
Now this is password is used to create PMK in message2.
when both sides has same inputs and same password so when they generate the keys those should be same as well. So if key matches in step3 with access point then its all good or it will fail.
normally if you enter wrong password and capture the traffic you will see it always fails at message2 because access point will never reply with message3 because keys did not match.
Hope this helps 🙂
Pingback:Wifi Hacking (Pt.1) - Redfox Security - Pen Testing Services
THANKS THIS IS POWERFUL POST
Thank you VERY MUCH, for this excellent explanation! I was always “afraid” of learning these concepts in depth, but you actually encouraged me to go even deeper. Thanks again!!!
Thanks for this article – it’s great to see semiconductor technology explained so clearly.
Pingback:[Wi-Fi] 4-way handshake 802.11i Security – 選擇實驗室